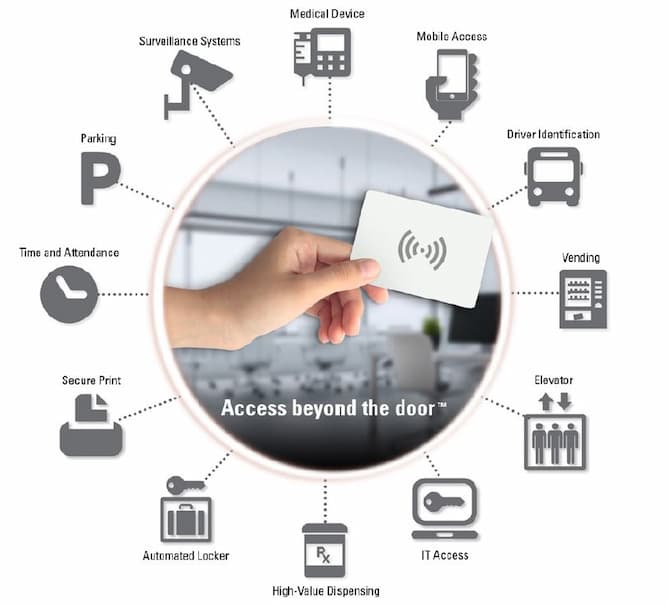
The Easy Way to a Smart Office
By Sean Houchin
“Smart office“ sounds like the future: hip technology companies and expensive new buildings. In fact, the first steps on the road to a smart office are easier than they seem. A good starting point is a modern access control system. It ensures security and, in combination with smartphone-based ID solutions, more productivity in everyday work. We reveal which aspects companies need to consider to make an implementation a success.
A good starting point to a smart office is a modern access control system.
ID cards and key fobs based on RFID have proven their worth in connection with access control. However, new solutions now also incorporate so-called mobile credentials. Digital smartphone credentials have clear advantages. For companies, they are easy to manage. For employees, they provide greater convenience by allowing the company cell phone to be used as a universal identification medium: electric vehicle charging, time recording, access to meeting rooms, logging on to the computer with single sign-on, secure printing, paying in the canteen — it all works completely seamlessly. Finally, employees save time that they can invest in value-adding activities. Simple access is provided by an app that implements the appropriate authorizations on the smartphone. This allows iOS and Android devices to communicate directly with RFID readers. Here are some tips to make a modern access control system a success.
Tip No. 1: Go for a holistic consulting approach
To ensure that the solution meets the expectations of users and operators, careful planning is the key. In the run-up to implementation, a whole series of questions must therefore be clarified, such as:
- Should access control be introduced for a single building or for different properties and possibly even across national borders?
- Are several technologies and credentials already in use?
- Which applications are to be covered?
- Comprehensive pre-sales consulting, therefore, includes an inventory and requirements analysis (including documentation of results), a feasibility study, proof-of-concept, and a project and rollout plan.
- In the implementation phase, hardware and software integration, application development, configuration and all customizations as well as testing and verification of protocols should be covered by the solution provider.
Tip No. 2: Invest in future security
Requirements and IT infrastructures change over time — and so does the overall system. Technical support must therefore not end with the initial integration. Only with a flexible system that provides for optimizations, adaptations and upgrades are companies also on the safe side in the future. As a solution provider, we at ELATEC, therefore, provide our customers with the DevPack software development kit. The versatile DevPack contains a range of tools that make it possible to easily adapt the products delivered in the standard configuration to specific requirements — even via remote access.
Tip No. 3: Look for flexibility
For companies with several office buildings, the introduction of a uniform access solution for all properties is worthwhile. After all, central remote maintenance of digital badges significantly reduces administrative effort. However, implementation can be a challenge, especially for companies with international operations. Often, different technologies are even in use from country to country. The solution: multi-frequency readers from ELATEC. The devices are compatible with up to 60 transponder technologies and certified for sale in up to 110 countries worldwide. The devices use RFID for authentication and access as well as NFC (Near Field Communication) or BLE (Bluetooth® Low Energy) technologies to integrate mobile devices into access control systems.
Tip No. 4: Make the system secure
Access control systems are designed to protect people and assets, so they must be secured against tampering. On the one hand, the physical security of the reader must be considered. On the other hand, the reader must support the credentials and encryption algorithms appropriate for the application’s security level. For effective and holistic security, not only the reader but the entire system must be included in the security concepts.
After a consistent implementation of the tips, all doors are open for a successful digital access control solution.
Would you like to know more about this topic? You can find more insights in our whitepaper.
Sean Houchin is the product manager for ELATEC Inc in Palm City, Florida and is part of the global ELATEC GmbH product management team. He has more than 20 years of experience in product development, management and applications engineering. Sean is an expert in RFID technology, optoelectronic and fiber optic video, audio, and data transmission equipment for military and commercial applications and is a veteran of the United States Navy.
More Posts
- RFID Kiosk, Biometrics & Identity Verification – Access Control Kiosk(Opens in a new browser tab)
- Elatec RFID Reader Kiosks Catalog(Opens in a new browser tab)
- Kiosk RFID News – Elatec U.S. Production Facility Ships First 100,000 RFID Units(Opens in a new browser tab)
- New mobile specific touchless mobile interaction RFID Readers ELATEC(Opens in a new browser tab)
VIDEO – Example for Elevator Access