Provision Holding secures 100% ownership of 650 kiosks in Rite Aid stores
US-based provider of integrated solutions for retail Provision Holding has secured 100% ownership of 650 kiosks in Rite Aid stores.
Source: www.retail-insight-network.com
Amazon Lockers vs. Walmart pickup tower: Which is better?
Amazon Lockers and Walmart’s pickup towers let shoppers pick up their products in-store and save on shipping. We tested them to see which was better.
Source: www.businessinsider.com
Good writeup on actually using both of the units. We were not surprised that Amazon won. Having used it at the local Whole Foods it was measured almost in single digit seconds to pickup. Looks like Walmart overthought it and over complicated it.
Why Healthy Vending Machines Are Trending
As our lives get busier and more and more people are working remotely than ever before, we find ourselves in a moment in history when vending machines make a lot of sense: They’re convenient, they’re fast, they’re affordable—and now, they’re finally getting healthier.
Source: www.mindbodygreen.com
Cash Or Card: Some Businesses Are Making Decision To Go Cashless « CBS Philly
Some consumers are making customers choice of paying with cash or credit easier by going cashless, but not everyone is on board with the idea.
Source: philadelphia.cbslocal.com
Kroger Launches Voice-Assistant Ordering for Grocery Ecommerce
Bloomberg – Online Stores Moving to Physical Stores – Why?
Matt Townsend, global business reporter for Bloomberg, on how digital natives like Warby Parker have recognized they need physical stores to grow and prosper. Hosted by Pimm Fox and Lisa Abramowicz.
Source: www.bloomberg.com
Nice talk on how online retailers are moving to brick and mortar and why. Costs primarily.
Enough With the U.S. Retail Apocalypse – Bloomberg
Not every company is rolling over as Amazon runs roughshod over the industry.
Source: www.bloomberg.com
Her “retail matrix” analyses four factors that affect retailers: brands, experiential, frictionless and low-cost. These ingredients largely determine success amid brutal competition.
Meanwhile, Kahn says, “digitally native vertical brands” have become big sellers. Niche brands like Warby Parker eyeglasses, Casper mattresses and Allbirds shoes are creating a very different shopping experience — and competing successfully against the retail behemoths.
Blind Marylanders sue Walmart, saying self-serve checkouts violate ADA – Baltimore Sun
Three blind Maryland residents and the National Federation of the Blind are suing Walmart.
Source: www.baltimoresun.com
Assisted checkout getting a bad name.
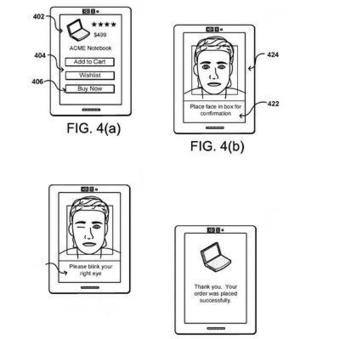
Amazon.com patents wink-controlled facial recognition technology for online shopping
The technology resembles iPhone X capabilities, which currently doesn’t allow purchases in Amazon’s marketplace.
Source: www.bizjournals.com
Several gesture technologies do this now (activate on wink). I am surprised Amazon got a patent on this process though it is an ordering process and not a navigation process for disabled.